Cybersecurity Controls for Jira
Introduction

Introducing the Cybersecurity Baseline Controls App, an enterprise-ready solution for small companies to enhance their security posture within Jira. This app provides a comprehensive set of baseline controls to safeguard against cyber threats, including regular security assessments, incident response planning, and vulnerability management. By implementing these best practices, companies can effectively protect their sensitive data and minimize the risk of a data breach. Additionally, the app is easily integrated into Jira, ensuring a seamless and efficient implementation process for businesses. Upgrade your company's cybersecurity with the Cybersecurity Baseline and ISO/IEC 27001 Controls App for Jira.
The Unicis Cybersecurity Controls application for Jira works with the following frameworks:
Demo
For more info please see the demo video (1:01 minute long):
Requirements
Unicis CSC is developed with Atlassian Forge platform. Hence, it can be only installed in Atlassian Jira Cloud product. It requires read, write, manage and storage access to your Jira account, because the CSC are stored in your Atlassian Cloud instance, and not shared with Unicis. Unfortunately, it can not be installed for Server and Data Jira set up.
Installation
You can install Unicis Cybersecurity Controls for Jira - Unicis.CSC from Atlassian Marketplace. After installation, you will be requested to grant and read access. Have in mind that Unicis CSC application requires a storage, manage, write and read access to your Jira account, however it does not share your data with Unicis. It stays with your Atlassian Jira account.
Configuration
To use the CSC app, you need to assign it to one or more Jira projects and set up one of the frameworks.
Keep in mind that multiple projects will have one dashboard, which means that only one security team can be in one company and the company will have one cybersecurity control.
Click on a drop-down menu and choose which Framework control your organization is following.
After you have selected a framework, the changes are saved.
Click on Apps on the top header, click on Manage your apps, on the side panel under APPS click Cybersecurity Control Settings and you will see the below screen.
To assign a Jira already existing project to be enabled for CSC you need to click on Add Project.
Multiple project can be added.
There are one actions available: Delete.
Delete
You can delete added project.
All cybersecurity controls related to this project will be erased.
Features
Cybersecurity Control app has a several features. Such as:
- You can enable the Unicis Cybersecurity Control app for Jira by assigning it to one or more Jira projects.
- You can designate several Jira tickets as a baseline or proof of evidence for each criterion, i.e. control and requirements.
- You can use a dedicated framework control in your organization.
- Utilizing the ISO/IEC 21827:2008 methodology for security maturity score, an interactive dashboard and overview of your company's security baseline posture are provided.
- Provide you with a filter feature on an interactive table based on the current state of the capability model for each area, control, and need.
CSC app works with any Jira project templates, for instance software project, service project, HR service manage, legal service management, etc. There is no limitation.
For more details please see subsections.
Dashboard
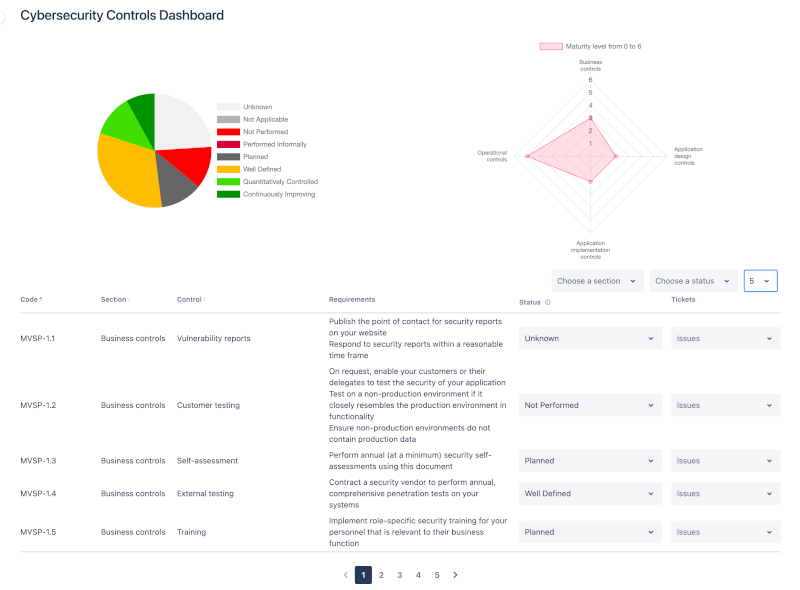
CSC provides you an overview dashboard for all the baseline cybersecurity controls that are assigned for the Jira Project.
There are two ways to reach the dashboard:
- If the project is a Jira Software project, select Cybersecurity Controls Dashboard on the left side of the screen.
- If it is a Jira Business project, select Cybersecurity Control Dashboard from the dropdown menu under Apps in the top menu.
Multiple assigned Jira projects will have one CSC dashboard, as a result of which only one security team, and have only one unified cybersecurity controls.
The dashboard is coupled of two sectoins.
Firstly, there are two charts:
- A pie chart illustrating the status of cybersecurity controls according to the proportion of controls.
- Radar charts show security maturity levels in accordance with ISO/IEC 21827:2008 methodology. Showing multiple data points and the variation between them.
Second section is a table with a list of controls:
- Code special example of a code: MVSP-1.1
- Section, for example, Business Controls, Application Design Controls, etc.
- Control name, for instance Training, Self-asessment, etc.
- Requirements that must be set up and put into practice
- Status, as detailed below. Dropdown option.
- Tickets related to the control, or proof to logs and proof of concept for the control's implementation. Dropdown option for Jira project issues.
A control may have various issues, or a control may be linked to several issues. No limitation.
Frameworks
The Cybersecurity Controls app is based on the following frameworks. See the frameworks documentation for a full list.
Minimum Viable Secure Product
Minimum Viable Secure Product - Controls is a minimal security checklist for B2B software and business process outsourcing suppliers, as well as controls for a Minimum Viable Secure Product.
The checklist was created with simplicity in mind and only includes the measures that must be put in place to guarantee a product has a minimally feasible security posture.
The controls should be implemented at a minimum by all businesses creating B2B software or otherwise managing sensitive information in the broadest sense, and doing more is strongly advised.
ISO/IEC 27001
The goal of an Information Security Management System (ISMS) is to protect the confidentiality & integrity of data and availability. You can use this control on any type of organization. This management system is based on the same high-level structure as other management systems.
The Unicis CSC application provides ISO/IEC 27001 revision controls, which were largely updated in the year 2013 and, most recently, in the year 2022.
The display controls can be filtered by parts using Choose a section or filter by status using Choose a status and the number of controls that will appear on each page, for instance: 5, 10, 25, 50 and 100.
NIST CSF2.0
The National Institute of Standards and Technology (NIST) Cybersecurity Framework (CSF) 2.0 Available is a voluntary framework designed to help organizations protect their information systems from cyberattacks. The framework provides a comprehensive set of guidelines and best practices that organizations can employ to effectively manage their cybersecurity program. It was developed in response to the increasing number of cyber threats and the need for organizations to be more prepared and resilient.
The Unicis CSC application provides NIST CSF 2.0.
The framework offers organizations a structured approach to evaluating cybersecurity risk and identifying areas for improvement. Each element includes activities and objectives that are important for successful cybersecurity program management.
Status
Maturity level is based on ISO/IEC 21827:2008 Information technology — Security techniques — Systems Security Engineering — Capability Maturity Model:
| Status | Meaning |
|---|---|
| Unknown | Has not even been checked yet |
| Not Applicable | Management can ignore them |
| Not Performed | Complete lack of recognizable policy, procedure, control etc. |
| Performed Informally | Development has barely started and will require significant work to fulfill the requirements |
| Planned | Progressing nicely but not yet complete |
| Well Defined | Development is more or less complete, although detail is lacking and/or it is not yet implemented, enforced and actively supported by top management |
| Quantitatively Controlled | Development is complete, the process/control has been implemented and recently started operating |
| Continuously Improving | The requirement is fully satisfied, is operating fully as expected, is being actively monitored and improved, and there is substantial evidence to prove all that to the auditors |
The pie chart and the radar map above the table will be recalculated if the status of one of the controls is changed.
Add CSC from Jira Issue
If you open the issue and click the CSC logo icon under the menu, you will be able to select a Control from the dropdown menu in the following format: CODE: Section, Control name, for example, MVSP-1.5: Business controls, Training, and requirements.
You can add and delete associated control from the issue by clicking + Add Control or Delete.

All of the issue's controls will be deleted if you click the Delete button. Please use the Trash symbol next to the dropdown control to delete a single control.
Activity/Audit Log
It can be accessed when you open the Jira ticket and on Activity sections click Activity logs of CSC.
We only display changes of the records, such as:
- Initial
- Created
- Added
- Removed
- Changed
The format of displaying the changes is as follows: Example 1:
[Author] created the Cybersecurity Controls 1/5/2023 3:29:09 PM (Date format M/DD/YYYY H:MM AM/PM)
Example 2:
[Author] changed the control M/DD/YYYY H:MM AM/PM
MVSP-1.1, Business controls, Vulnerability reports → MVSP-1.3, Business controls, Self-assessment
Pricing
Please check the Atlassian Cloud app pricing overview.
Permissions
Unicis - Transfer Impact Assessment can perform the following actions on behalf of the user:
- App Storage scope
- Read and write to app storage service
- Create and manage issues
- Create and edit issues in Jira, post comments as the user, create worklogs, and delete issues.
- Manage project settings
- Create and edit project settings and create new project-level objects (e.g. versions and components).
- View active user profile
- View the profile details for the currently logged-in user.
- View Jira issue data
- Read Jira project and issue data, search for issues, and objects associated with issues like attachments and worklogs.
- Before you revoke permissions, we recommend you to notify the user as they will lose access to the app.
Technical details
Transfer Impact Assessment (TIA) is build in Atlassian Forge UI kit components with the following components:
It requires the following permissions scope:
- read:jira-work
- write:jira-work
- manage:jira-project
- storage:app
Changelog
v.2.5.0
Minor bug fixes and improvement.
v.2.4.0
Added new NIST Cybersecurity Framework 2.0
v.2.3.0
Implement Dark Theme.
Implementing ISO/IEC 27001:2013 and ISO/IEC 27001:2022 security controls.
v.2.2.0
Patched security vulnerability
v2.13.0
Minor fixes
v2.1.0
First release with MVP scope
