Cybersecurity Controls

Subscription plan availability:
- MVSP v1.0-20211007 — Community default framework available to all users
- GDPR — available in the Community plan.
- ISO/IEC 27001 — available in the Premium plan.
- EU NIS2 Directive — available exclusively in the Premium plan.
- CIS Critical Security Controls v8.1 — available in the Premium plan.
- C5 Framework — available in the Premium plan.
- SOC 2 — available exclusively in the Ultimate plan.
- NIST CSF 2.0 — available in the Ultimate plan.
The Cybersecurity Management System is a comprehensive set of baseline controls to safeguard against cyber threats, including regular security assessments, incident response planning, and vulnerability management. By implementing these best practices, companies can effectively protect their sensitive data and reduce the risk of a data breach.
You will see the following screen depending on the Cybersecurity control framework you selected in Settings.

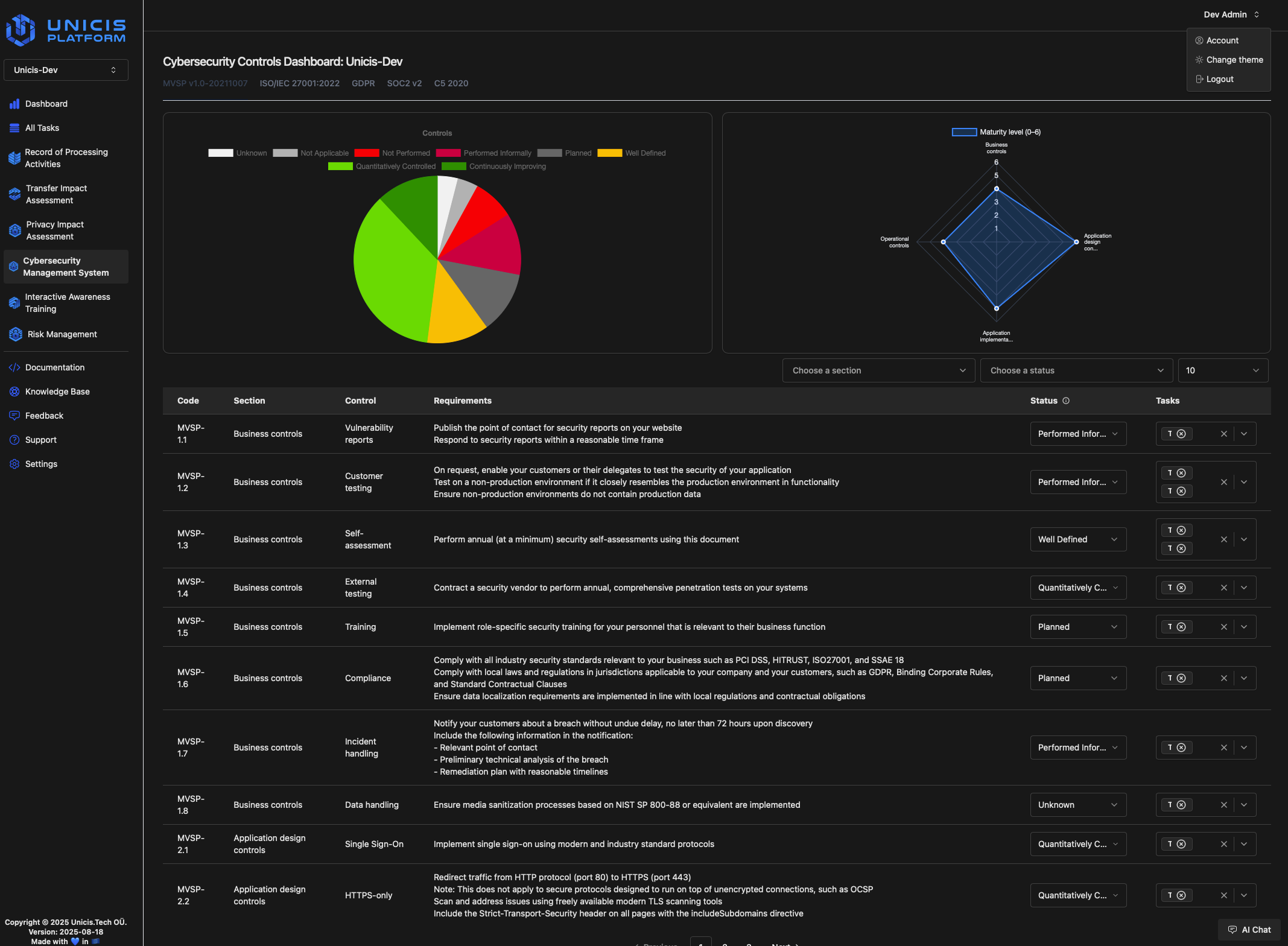
The Cybersecurity Management System dashboard is coupled of two sectoins.
Firstly, there are two charts:
- A pie chart illustrating the status of cybersecurity controls according to the proportion of controls.
- Radar charts show security maturity levels in accordance with ISO/IEC 21827:2008 methodology. Showing multiple data points and the variation between them.
Second section is a table with a list of controls:
- Code special example of a code: MVSP-1.1
- Section, for example, Business Controls, Application Design Controls, etc.
- Control name, for instance Training, Self-asessment, etc.
- Requirements that must be set up and put into practice
- Status, as detailed below. Dropdown option.
- *Tickets/Tasks related to the control, or proof to logs and proof of concept for the control's implementation. Dropdown option for team tasks.
A control may have various tasks, or a control may be linked to several tasks. No limitation.
Frameworks
The Cybersecurity Controls app is based on the following frameworks. See the frameworks documentation for a full list.
When multiple frameworks are selected, corresponding tabs will appear in the chart view above, allowing you to navigate between frameworks seamlessly.
Minimum Viable Secure Product
Minimum Viable Secure Product - Controls is a minimal security checklist for B2B software and business process outsourcing suppliers, as well as controls for a Minimum Viable Secure Product.
The checklist was created with simplicity in mind and only includes the measures that must be put in place to guarantee a product has a minimally feasible security posture.
The controls should be implemented at a minimum by all businesses creating B2B software or otherwise managing sensitive information in the broadest sense, and doing more is strongly advised.
Available on Community subscription plan.
GDPR (General Data Protection Regulation)
The General Data Protection Regulation (GDPR) is a legal framework enacted by the European Union to ensure the protection of personal data of individuals. It applies to all organizations processing personal data of EU residents, regardless of their location.
The regulation outlines strict requirements for data privacy, user consent, breach notifications, data subject rights, and more. Compliance helps organizations mitigate legal risks and strengthen trust with users.
The Unicis CSC application provides a mapped set of GDPR requirements and implementation guidance, focusing on practical steps to fulfill key obligations like data minimization, accountability, and data protection by design and by default.
Available only on Community subscription plan.
ISO/IEC 27001
The goal of an Information Security Management System (ISMS) is to protect the confidentiality & integrity of data and availability. You can use this control on any type of organization. This management system is based on the same high-level structure as other management systems.
The Unicis CSC application provides ISO/IEC 27001 revision controls, which were largely updated in the year 2013 and, most recently, in the year 2022.
The display controls can be filtered by parts using Choose a section or filter by status using Choose a status and the number of controls that will appear on each page, for instance: 5, 10, 25, 50 and 100.
Available on Premium subscription plan.
EU NIS2 Directive
The EU NIS2 Directive is the European Union’s latest legislation aimed at enhancing cybersecurity across critical infrastructure sectors and digital service providers. It replaces the original NIS Directive with expanded scope, stricter supervision, and higher security requirements.
NIS2 introduces risk management measures, incident reporting obligations, and board-level accountability. It affects a wider range of entities, including medium and large companies in sectors such as energy, transport, health, digital infrastructure, and public administration.
The Unicis CSC application offers structured control mappings to help organizations implement and maintain compliance with NIS2 obligations, including governance, technical, and operational safeguards.
Available only on Premium subscription plan.
CIS Controls v8.1 (Center for Internet Security)
The CIS Critical Security Controls (v8.1) are a prioritized and actionable set of cybersecurity best practices designed to help organizations reduce risk. Developed by experts in the field, the controls are based on real-world threats and are continuously updated to reflect evolving risks.
CIS v8.1 includes 18 top-level controls covering areas such as asset inventory, access control, vulnerability management, secure configuration, and incident response.
The Unicis CSC application provides comprehensive access to CIS Controls v8.1, enabling organizations to assess and improve their cybersecurity maturity using clear, measurable, and prioritized steps.
Available only on Premium subscription plan.
C5 (Cloud Computing Compliance Controls Catalogue)
The C5 Framework — developed by the German Federal Office for Information Security (BSI) — provides a standardized approach to assessing and demonstrating the security of cloud service providers. It serves as a recognized benchmark for ensuring transparency and trust in cloud security practices.
C5 defines a comprehensive catalog of controls across key domains such as data protection, service availability, incident management, and compliance with applicable laws. It is especially relevant for organizations operating or relying on cloud-based services that need to demonstrate compliance with European security expectations.
The Unicis CSC application includes the C5 control mappings to help organizations verify that their cloud environments meet baseline security and compliance requirements.
Available on Premium subscription plan.
NIST CSF2.0
The National Institute of Standards and Technology (NIST) Cybersecurity Framework (CSF) 2.0 Available is a voluntary framework designed to help organizations protect their information systems from cyberattacks. The framework provides a comprehensive set of guidelines and best practices that organizations can employ to effectively manage their cybersecurity program. It was developed in response to the increasing number of cyber threats and the need for organizations to be more prepared and resilient.
The Unicis CSC application provides NIST CSF 2.0.
The framework offers organizations a structured approach to evaluating cybersecurity risk and identifying areas for improvement. Each element includes activities and objectives that are important for successful cybersecurity program management.
Available only on Ultimate subscription plan.
SOC 2 (Service Organization Control 2)
The SOC 2 framework, developed by the American Institute of Certified Public Accountants (AICPA), focuses on managing customer data based on five Trust Service Criteria: security, availability, processing integrity, confidentiality, and privacy.
SOC 2 is particularly relevant for service providers that store or process customer data in the cloud. It emphasizes continuous monitoring, documentation, and reporting on the organization’s internal controls related to data handling and operational effectiveness.
The Unicis CSC application provides mapped SOC 2 controls aligned with the Trust Services Criteria, helping organizations assess, implement, and monitor security and compliance measures required for SOC 2 readiness or certification.
Available only on Ultimate subscription plan.
Status
Maturity level is based on ISO/IEC 21827:2008 Information technology — Security techniques — Systems Security Engineering — Capability Maturity Model:
| Status | Meaning |
|---|---|
| Unknown | Has not even been checked yet |
| Not Applicable | Management can ignore them |
| Not Performed | Complete lack of recognizable policy, procedure, control etc. |
| Performed Informally | Development has barely started and will require significant work to fulfill the requirements |
| Planned | Progressing nicely but not yet complete |
| Well Defined | Development is more or less complete, although detail is lacking and/or it is not yet implemented, enforced and actively supported by top management |
| Quantitatively Controlled | Development is complete, the process/control has been implemented and recently started operating |
| Continuously Improving | The requirement is fully satisfied, is operating fully as expected, is being actively monitored and improved, and there is substantial evidence to prove all that to the auditors |
The pie chart and the radar map above the table will be recalculated if the status of one of the controls is changed.
Add
In the Tasks edit mode the Cybersecurity Controls tab allows you to add cybersecurity control to a task.
- Please select a control from a dropdown option
- Add a Status
- Read more about control requirements
- You can add more controls to a task with the + Add Control button
- One may also opt to eliminate a control by clicking on the Remove button.
There is no limit to the controls that can be associated with a task. Consider the task as an evidence, sometimes one evidence can provide proof for multiple controls depending on the framework.
Delete
Activity logs
It can be accessed when you open the associated ticket and on Audit logs sections click Cybersecurity Audit logs.
We only display changes of the records, such as:
- Created
- Deleted
- Updated